Production MCP Gateway for Fintech: Open Source vs Enterprise
Explore the trade-offs between open-source and enterprise MCP gateways for fintech, focusing on compliance, security, and cost-effectiveness.
Production MCP Gateway for Fintech: Open Source vs Enterprise
An MCP gateway routes requests between AI clients and Model Context Protocol servers while enforcing security policies, OAuth authentication, and audit logging—transforming experimental AI deployments into production-ready infrastructure that meets fintech compliance requirements. Open-source options like Docker's containerized gateway offer flexibility but require internal teams to build SSO and audit controls, while enterprise platforms like MintMCP bundle SOC2-aligned governance with 99.99% uptime guarantees.
TLDR
- MCP gateways provide the OAuth protection, audit trails, and enterprise authentication needed to move AI deployments from demos to production in regulated fintech environments
- Open-source gateways (Docker MCP, Kong OSS) deliver strong performance—Kong handles 54,250 TPS with sub-30ms latency—but shift security hardening and maintenance to internal teams
- Enterprise solutions bundle SOC2 certification and GDPR-compliant logging, with initial deployments requiring 3-6 months and $150K-$500K investment
- Security analysis found command injection flaws in 43% of MCP servers, making gateway-level controls essential for blocking prompt injection and tool poisoning
- Total cost of ownership often favors enterprise subscriptions once teams need 99.99% uptime and regulator-ready evidence, despite higher upfront licensing costs
An MCP gateway sits between your AI clients and Model Context Protocol servers, routing requests, enforcing security policies, and logging every tool invocation so regulated fintech teams can move from local demos to auditor-ready infrastructure. As adoption accelerates, enterprises face a pivotal choice: run an open-source gateway and absorb internal DevOps costs, or subscribe to an enterprise platform that bakes in OAuth 2.1, SOC2 audit trails, and multi-region failover. This post unpacks the trade-offs so CISOs and platform leads can pick the right path for their AI roadmaps.
Why Fintech Needs a Production-Grade MCP Gateway
"Financial institutions face mounting pressure to deploy AI capabilities while maintaining the security, compliance, and governance that regulators demand."
Model Context Protocol provides the standardized infrastructure most banking executives consider strategic, enabling AI assistants to access customer data, transaction systems, and analytical tools without custom integrations. Yet running MCP in production is another matter entirely. As MCP adoption accelerates, enterprises quickly find themselves managing server sprawl, new attack surfaces, and rising complexity.
The MCP gateway transforms this protocol from a developer utility to production-grade infrastructure with OAuth protection, audit trails, and enterprise authentication. Without that layer, 65% of financial institutions cite data security as the primary AI adoption barrier, stalling roadmaps that could otherwise cut compliance workloads by 50-70%.
Key takeaway: A production MCP gateway is the compliance on-ramp that turns AI experiments into regulator-ready deployments.
What Are the Strengths and Pitfalls of Open-Source MCP Gateways?
Open-source gateways offer speed, transparency, and zero licence fees, but they shift security, SSO, and maintenance onto your team.
Strengths:
- Performance: Kong Enterprise achieved 54,250 transactions per second with 100% success and sub-30 ms latency in GigaOm benchmarks. Tyk, written in Go, outperforms Kong on major clouds in RPS and P99 metrics.
- Flexibility: APISIX, built on OpenResty, gains popularity for its plugin architecture and performance.
- Community innovation: Kong has powered trillions of API transactions since going open source in 2015.
Pitfalls:
- Hidden labour costs: IDC notes that while many organisations choose open source believing it is less expensive, calculating total cost of ownership is complex because there are so many variables.
- Security gaps: Docker security researchers found command injection flaws in 43% of analyzed MCP servers, meaning self-hosted teams must harden every deployment.
- Spec churn: The MCP specification updates frequently; you need ongoing investments to maintain compliance.
Docker MCP Gateway
Docker's open-source MCP Gateway acts as a centralized proxy, managing configuration, credentials, and access control. It runs MCP servers in isolated containers with restricted privileges, network access, and resource usage. Built-in logging and call-tracing provide visibility, yet Docker's approach does not include OAuth or SOC2-aligned controls out of the box. Teams still need to layer enterprise IAM and audit tooling on top.
Gravitee AM + APIM
Gravitee Access Management is a flexible, lightweight open-source IAM solution based on OAuth2, OpenID Connect, and SAML 2.0. Its audit trail feature records client authentication and MFA events, storing logs in MongoDB, JDBC, file, or Kafka reporters. Plugin extensibility lets you add connectors, policies, and identity providers, but regulated fintech teams must still build and maintain SSO integrations, secret management, and HA clusters internally.
When Do Enterprise MCP Gateways Beat DIY?
Enterprise MCP gateways shine when you need regulator-ready evidence, multi-region uptime, and dedicated support without staffing a platform team.
- Governance out of the box: Enterprise gateways provide SOC2 Type II certification, GDPR-compliant audit trails, and OAuth/SAML enforcement required for financial services regulation.
- Unified control plane: Kong AI Gateway and Konnect deliver enterprise-grade governance, visibility, and cost control for agentic workflows.
- Reduced DevOps burden: IBM's ContextForge MCP Gateway is an open-source feature-rich gateway aiming for enterprise environments, while Peta targets zero-trust security and human-in-the-loop approvals.
Case Study: MintMCP Gateway Roll-Out
MintMCP Gateway transforms local MCP servers into production-ready services with OAuth protection, real-time monitoring, and SOC2 Type II-aligned governance. Initial deployments require 3-6 months with an investment of $150K-$500K, but institutions see measurable improvements within the first quarter.
The gateway delivers:
- Per-user authentication to track exactly who accessed what data
- Granular tool access control (enable read-only operations, exclude write tools)
- Complete audit trail of every query and data access
- High availability with automatic failover for critical reporting
Key takeaway: Enterprise gateways front-load compliance investment so you can show auditors evidence, not excuses.
How Do MCP Gateways Block Prompt Injection and Pass Audits?
MCP's flexibility introduces new attack vectors that traditional perimeter controls miss.
Palo Alto Networks identifies five critical attack vectors: hidden instructions (prompt injection), tool shadowing and impersonation, excessive agency and privilege escalation, data exfiltration through legitimate channels, and rugpull trust exploitation. Docker's security analysis found that 43% of analyzed servers had command injection flaws.
Gateway-level mitigations:
| Control | How It Helps |
|---|---|
| Allowlisting | Restricts which tools agents can invoke |
| Runtime enforcement | Blocks suspicious calls in real time |
| Proxy communication layer | Manages agency and intercepts malicious payloads |
| Audit logging | Every MCP call logged with who, what, when, where, and result |
Gravitee AM's audit trail captures client authentication and MFA events so administrators can understand where authentication flows fail. FINOS released a vendor-agnostic AI Governance Framework outlining 15 risks and 15 controls specifically tailored for LLM-based systems in financial services, giving CISOs a peer-reviewed checklist.
OAuth 2.1 with PKCE is the emerging standard for HTTP-based MCP auth. MCP Auth SDK supports the MCP authorization specification version 2025-06-18, operating in resource server mode while relying on external authorization servers. Enterprise gateways like MintMCP and Kong enforce OAuth/SAML, eliminating the need to hand-roll token validation.
Open Source vs Enterprise MCP: What's the Real Total Cost?
Licence fees are only the tip of the iceberg. IDC warns that organisations choosing open source believing it is less expensive overlook upfront infrastructure, customization, and security-related costs.
Cost drivers for DIY open source:
- Initial build: Engineering hours for OAuth, audit logging, HA, and monitoring
- User support: Scales sub-linearly but still requires baseline support effort
- Spec maintenance: The MCP specification updates frequently, demanding ongoing compliance investments
- Security hardening: In-house expertise for customization and vulnerability patching
A World Bank focus note found that open-source software appears in nearly 97% of codebases, yet core fintech deployments remain early-stage because institutions need significant expertise and must align long-term goals with chosen solutions.
Enterprise value proposition: Enterprise subscriptions bundle data privacy assurances, governance, model risk management, latency guarantees, and uptime into predictable spend. As AI API pricing compresses, enterprise value now accrues from governance and multi-model orchestration, not raw inference costs.
Gartner IT spending benchmarks recommend using transparency and regular calibration as a best practice. For most regulated fintech teams, the math favours an enterprise subscription once you exceed pilot stage or need 99.99% uptime and regulator-ready evidence.
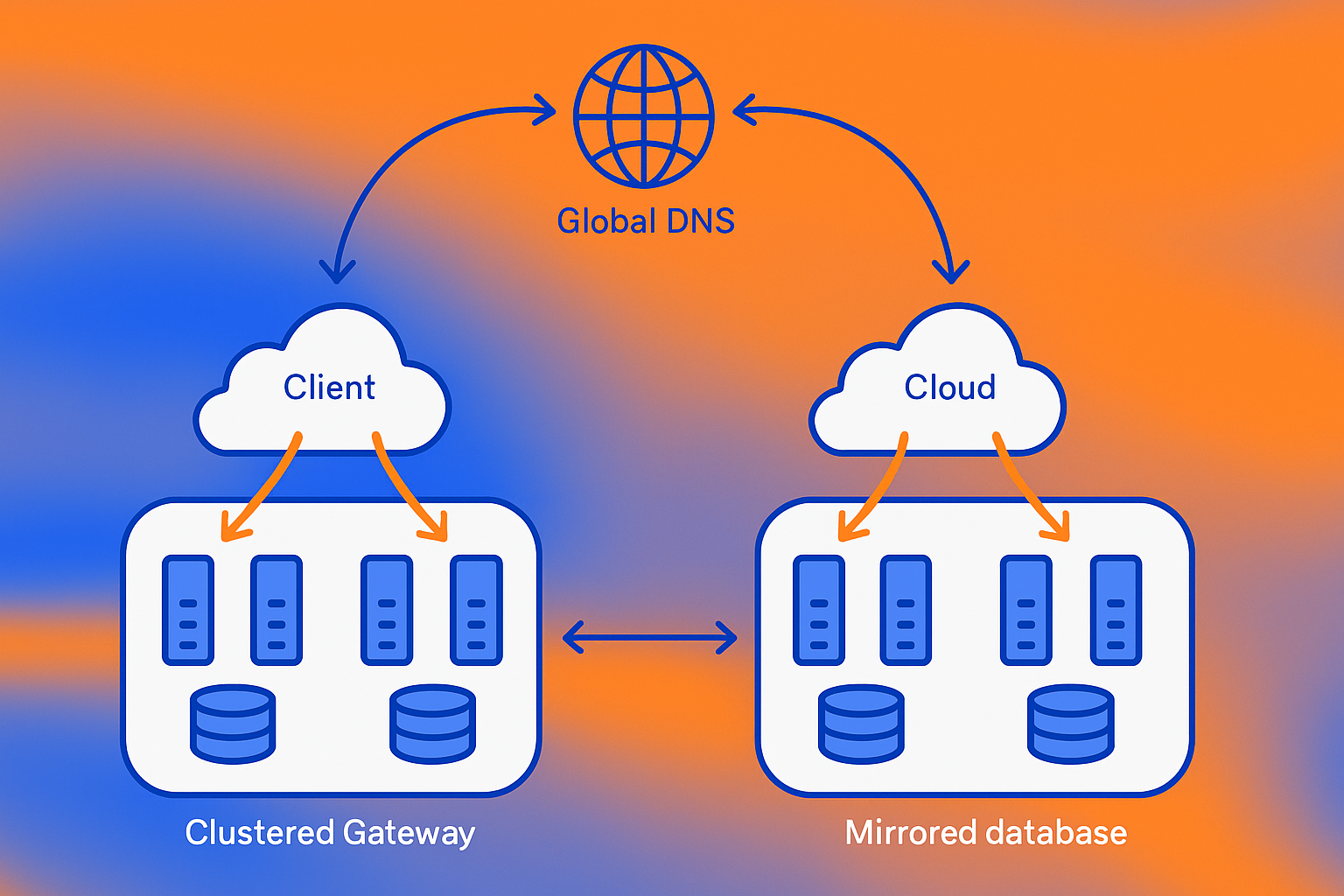
How Can You Hit 99.99% Uptime with MCP Gateways?
High availability for MCP gateways borrows patterns from API management: multi-region active-active, automated failover, and comprehensive monitoring.
AWS guidance demonstrates a multi-region resilient microservice architecture with active-active state across two regions. Amazon Route 53 failover records use Application Recovery Controller health checks to route requests, while Aurora global databases and DynamoDB global tables replicate data.
MuleSoft Flex Gateway supports multiple multi-region strategies:
- Active-active DNS: Each region services traffic at all times for high availability
- Active-passive DNS: Redirects traffic only if the primary region fails
- Latency-based routing: Directs requests to the closest region
Architecture checklist:
- Deploy gateway replicas across at least two availability zones
- Use load balancers with health-check-driven failover
- Replicate configuration and secrets to standby clusters
- Integrate observability (Grafana MCP Observability, Envoy AI Gateway metrics) to track session establishment, tool invocation frequency, and communication latency
Decision Framework: Picking the Right Gateway for Your Roadmap
Step 1: Assess compliance posture
Does your team already hold SOC2 Type II certification? If not, an enterprise gateway with audit logging of who, what, when, where, and result accelerates evidence collection.
Step 2: Estimate internal capacity
Open source demands DevOps bandwidth for OAuth, HA, and spec updates. Docker provides sandboxed isolation, but you still build the control plane. If your platform team is stretched, lean enterprise.
Step 3: Map scale trajectory
65% of financial institutions cite data security as the primary AI adoption barrier. Once you clear pilot and hit production traffic, enterprise SLAs de-risk the expansion.
Step 4: Evaluate governance needs
Do you need per-tool policies, human-in-the-loop approvals, or environment isolation? Enterprise gateways bundle these; open source requires custom coding.
Step 5: Compare TCO over 3 years
Factor in engineering hours, support scaling, and opportunity cost. "While you may never be able to come up with an accurate total cost of ownership because there are so many variables, doing your due diligence will point out your relative strengths and weaknesses in different cost centers and that should inform your decision," says Michele Rosen at IDC.
Key Takeaways
- An MCP gateway is essential for moving from AI demos to production in regulated fintech, providing OAuth protection, audit trails, and enterprise authentication.
- Open-source gateways (Docker MCP, Gravitee, Kong OSS) deliver performance and flexibility but shift security hardening, SSO, and spec maintenance onto internal teams.
- Enterprise gateways (MintMCP, Kong Konnect, IBM ContextForge) bundle SOC2 certification, GDPR-compliant logging, and HA, reducing DevOps overhead and accelerating audits.
- Security controls must address prompt injection, tool poisoning, and privilege escalation; gateway-level allowlisting, runtime enforcement, and proxy communication layers are table stakes.
- Total cost of ownership for open source often exceeds licence savings once you account for build, support, and maintenance; enterprises that need 99.99% uptime and regulator-ready evidence typically favour managed subscriptions.
If your team is evaluating MCP gateway options, Golf's platform provides protocol-aware observability and intent-driven security controls purpose-built for regulated industries. Deploy a single-workflow MCP server today and unblock your AI roadmap without breaching compliance.
Frequently Asked Questions
What is an MCP gateway and why is it important for fintech?
An MCP gateway acts as a mediator between AI clients and Model Context Protocol servers, ensuring secure, compliant, and efficient data handling. It's crucial for fintech to maintain regulatory compliance while deploying AI capabilities.
What are the benefits of using an open-source MCP gateway?
Open-source MCP gateways offer speed, transparency, and no license fees. They provide flexibility and community-driven innovation but require internal teams to manage security, SSO, and maintenance.
Why might a fintech company choose an enterprise MCP gateway over open-source?
Enterprise MCP gateways offer built-in compliance features like SOC2 certification, GDPR-compliant audit trails, and OAuth/SAML enforcement, reducing the DevOps burden and providing regulator-ready evidence.
How do MCP gateways help in preventing prompt injection attacks?
MCP gateways use allowlisting, runtime enforcement, and proxy communication layers to block suspicious calls and manage agency, thus preventing prompt injection and other security threats.
What factors should be considered when choosing between open-source and enterprise MCP gateways?
Consider compliance needs, internal capacity for DevOps, scale trajectory, governance requirements, and total cost of ownership over three years to make an informed decision.
Sources
- https://www.docker.com/blog/mcp-security-explained/
- https://www.mintmcp.com/blog/mcp-financial-brands
- https://konghq.com/resources/reports/mcp-gateway
- https://gigaom.com/report/api-and-microservices-management-benchmark-3/
- https://tyk.io/performance-benchmarks/
- https://medium.com/@dvirsegal/api-gateway-benchmarks-2025-b1be0baa7ae1
- https://my.idc.com/getdoc.jsp?containerId=US51834224
- https://mcpmanager.ai/resources/build-or-buy-mcp-gateway/
- https://docker.com/blog/build-to-prod-mcp-servers-with-docker
- https://documentation.gravitee.io/am/4.0
- https://documentation.gravitee.io/am/guides/audit-trail
- https://bytebridge.medium.com/why-mcp-adoption-stalls-and-how-to-fix-it-c6133bf95def
- https://www.mintmcp.com/blog/mcp-fintech-brands
- https://www.paloaltonetworks.com/resources/guides/simplified-guide-to-model-context-protocol-vulnerabilities
- https://www.finos.org/press/common-controls-for-ai-services
- https://mcp-auth.dev/docs
- https://fastpayments.worldbank.org/sites/default/files/2025-02/Open%20Source%20FPS_Focus%20Note_Final.pdf
- https://medium.com/@peter_32179/the-race-to-zero-in-ai-api-pricing-a-comprehensive-analysis-of-market-dynamics-strategic-3b7c3d3e3c1a
- https://www.gartner.com/en/information-technology/research/it-budgets
- https://aws.amazon.com/solutions/guidance/multi-region-resilient-microservice-on-aws
- https://docs.mulesoft.com/gateway/latest/flex-architecture-multi-region
