MCP Gateway for Fintech Compliance (2025)
Discover how MCP Gateways streamline fintech compliance, ensuring secure, compliant endpoints without code rewrites. Deploy at scale today.
MCP Gateway for Fintech Compliance (2025)
MCP Gateways provide a lightweight proxy layer that converts legacy financial APIs into compliant, observable endpoints without code changes, addressing the critical gap where 492 exposed MCP servers lack authentication while PCI DSS fines range from $5,000 to $100,000 monthly for non-compliance. The gateway enforces token delegation, audit logging, and pre-authentication to maintain PCI DSS and Open Banking controls as agentic AI traffic scales.
At a Glance
• Compliance risk: 74% of exposed MCP servers run on major cloud providers, creating immediate audit failures for fintech companies without authentication proxies
• Three-layer architecture: MCP Gateways implement proxy conversion, user-specific token delegation, and tamper-proof observability with only 3-4ms latency overhead
• 2025 regulatory pressure: PCI DSS 4.0.1, OFDSS (79 security requirements), and Open Banking guidelines all require encrypted transport and audit trails
• Agentic commerce scale: Visa and Mastercard project $180 billion in annual agentic AI transactions, requiring protocol-level trust verification
• Zero-intrusion deployment: Configuration-driven YAML setup works across bare metal, VMs, ECS, and Kubernetes without infrastructure modifications
• Security imperative: 72% of MCPs allow sensitive operations like code execution, with exploitation risk reaching 92% when installing 10 plugins
With breach costs climbing and regulators tightening the screws, fintech leaders need a faster path to audit readiness. The MCP Gateway is emerging as that shortcut: a lightweight proxy layer that converts legacy APIs into compliant, observable endpoints without rewriting code.
This guide breaks down why MCP Gateways matter now, what the 2025 compliance stack demands, and how to deploy one at scale.
Why Do MCP Gateways Matter for Fintech Right Now?
The Model Context Protocol (MCP) is "one of the most important evolutions in AI infrastructure today. It allows large language models (LLMs) to interact with external tools and APIs in a structured way, turning them from passive text generators into active agents that can fetch data, trigger workflows, and execute tasks on behalf of users," according to WorkOS.
That flexibility creates risk. Security researchers found 492 MCP servers with no client authentication or traffic encryption. Approximately 74% of those servers sit on major cloud providers like AWS, Azure, and GCP.
For fintech teams, the math is brutal. PCI DSS is a set of security standards designed to ensure that all companies that accept, process, store, or transmit credit card information maintain a secure environment. Failure to comply can result in fines ranging from $5,000 to $100,000 per month until compliance is achieved.
An MCP Gateway solves the exposure problem by sitting between AI agents and sensitive financial systems. It enforces token delegation, audit logging, and pre-authentication, keeping PCI DSS and Open Banking controls intact even as agentic traffic scales.
Key takeaway: If you are running MCP servers without an authentication proxy, you are one misconfiguration away from a compliance failure.
What Is the 2025 Compliance Stack—PCI DSS, OFDSS, and Open Banking?
Three frameworks now define the fintech compliance baseline.
PCI DSS 4.0.1 took full effect in March 2024, retiring version 3.2.1. To become PCI compliant, a payment gateway must adhere to the 12 requirements outlined by the PCI Security Standards Council. These include installing and maintaining a firewall configuration, encrypting transmission of cardholder data across open networks, and maintaining a policy that addresses information security for all personnel.
OFDSS (Open Finance Data Security Standard) establishes 79 individual security requirements across 13 control domains that address common data security risks. It targets cloud-native, digital finance companies that outgrow generic security frameworks.
Open Banking guidelines help Third Party Providers deliver "innovative, competitive and secure products and services within the evolving Open Banking Ecosystem," according to the Open Banking Standards. These guidelines bring focus to critical operational factors around security, data custody, and proposition testing.
The three frameworks overlap on a handful of non-negotiables:
- Encrypted transport (TLS 1.2+)
- Strong access controls
- Provable audit trails
- Sender-constrained tokens
An MCP Gateway centralizes all four duties in a single enforcement point.
Agentic Commerce Pressure
Visa and Mastercard are not waiting for regulators to catch up. Both networks launched agentic AI payment tools designed to verify AI agents and process transactions with less friction.
Agentic AI commerce could top $180 billion annually, according to Digital Commerce 360. Visa's Trusted Agent Protocol is designed to enable agentic commerce at scale with a framework where an agent can "facilitate verifiable trust over existing web infrastructure (HTTP), with minimal changes required to existing merchant systems" and "securely carry various forms of payment credentials" while communicating "over a variety of channels (e.g., web, API) and protocols (e.g., MCP, ACP)," per the Visa developer specifications.
Mastercard's Agent Pay Merchant Acceptance Framework emphasizes no-code integration. "As AI agents become more capable and autonomous, the need for trust, transparency and interoperability becomes paramount," stated Mastercard's Fourez in a Digital Commerce 360 report.
If Visa and Mastercard are building protocol-level trust into agentic payments, fintechs that skip gateway-layer controls will find themselves on the wrong side of scheme audits.
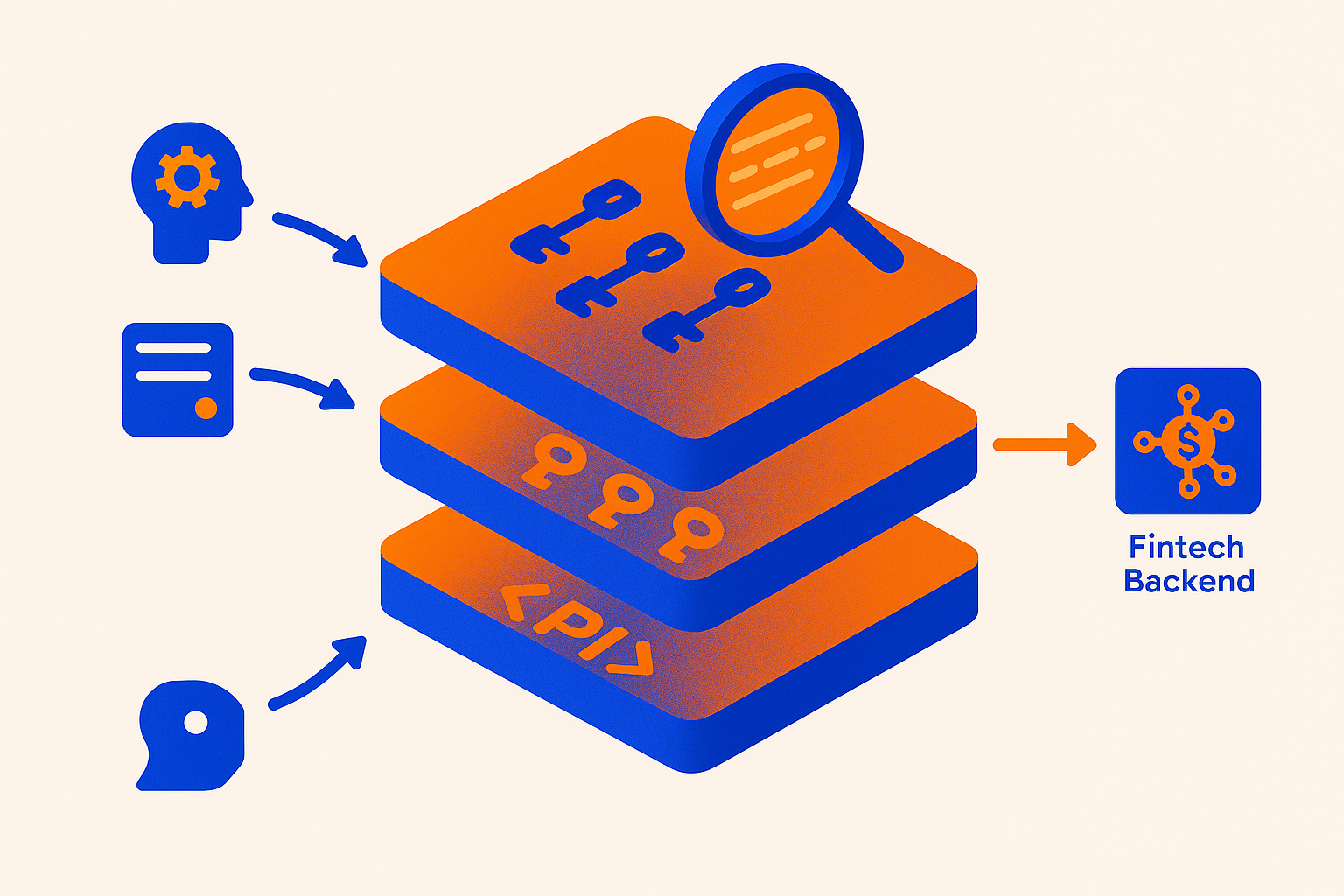
How Does an MCP Gateway Work: Proxy, Delegation, and Observability Layers?
An MCP Gateway is "a lightweight gateway service that instantly transforms existing MCP Servers and APIs into MCP servers with zero code changes," according to the mcp-gateway repository. It features Docker deployment and a management UI, requiring no infrastructure modifications.
The architecture breaks into three layers:
| Layer | Function |
|---|---|
| Proxy | Converts RESTful APIs, gRPC, and WebSocket endpoints to MCP-compliant services via YAML configuration |
| Delegation | Grants user-specific access tokens so each request operates within the user's permission scope |
| Observability | Logs every tool call for tamper-proof storage and audit retrieval |
Token delegation is the linchpin. It "enhances server security for several reasons. It grants user-specific access, wherein each request operates within the user's permission scope," notes Trend Micro.
The gateway supports:
- OAuth-based pre-authentication for MCP servers
- Multi-replica service deployments
- Kubernetes and Helm integration
- Zero intrusion into existing infrastructure (bare metal, VMs, ECS, Kubernetes)
Latency overhead is minimal. Research on MCP Guardian, a related security middleware, showed the framework "introduced an absolute increase of about 3–4 ms in median latency" while blocking 100% of unauthorized tokens and malicious commands, per an academic study.
Comprehensive Audit Trails
Audit trails are not optional in fintech. "Comprehensive audit trails involve capturing, recording, and storing every action taken across your environment," states AWS Well-Architected guidance. "This provides a log of evidence that can offer insights for security and audit teams, aiding in identifying suspicious activities, evidencing non-compliance, and uncovering the root cause of issues."
HCX protocol instances, for example, are expected to "log each API call received along with the non encrypted details (domain headers, sig/enc algorithm details, sender & recipient details) and status of signature verification," according to HCX Technical Specifications. The audit information must be accessible through an API so participating systems can query logs related to them.
AWS services like CloudWatch Logs can monitor, store, and access log files from EC2 instances, CloudTrail, Route 53, and other sources. Logs can be processed in near real-time and delivered to Amazon OpenSearch, Kinesis, Firehose, or Lambda for custom processing.
Best practices for audit storage:
- Centralize evidence in a secure, accessible location for easy retrieval during audits
- Enforce access controls to maintain integrity and confidentiality
- Implement controls to prevent deletion, overwriting, or tampering
- Conduct regular audits of your audit systems
How Do You Block the Top MCP Threats Before Regulators Notice?
MCP connections create bridges between untrusted model-generated inputs and sensitive systems. "A single weak point (a poisoned prompt, an overbroad permission, or an unverified endpoint) can turn that bridge into a pathway for exploitation," warns WorkOS.
The threat landscape is quantified:
- 72% of MCPs allow sensitive operations such as writing to disk, executing code, or calling high-permission APIs
- Installing 10 MCP plugins pushes the exploitation risk to 92%, per Pynt research
- 49% increase in web attacks against applications and APIs between Q1 2023 and Q1 2024
Palo Alto Networks identifies five critical attack vectors:
- Hidden Instructions (Prompt Injection)
- Tool Shadowing and Impersonation
- Excessive Agency and Privilege Escalation
- Data Exfiltration Through Legitimate Channels
- Rugpull and Trust Exploitation
Mitigation requires a robust security strategy with detailed recommendations on allowlisting, guaranteed runtime security enforcement, and deploying a proxy MCP communication layer to manage agency and prevent attacks.
Why MFA & Sender-Constrained Tokens Still Rule
FFIEC guidance is clear: "When a risk assessment indicates that single-factor authentication with layered security is inadequate, multi-factor authentication (MFA) or controls of equivalent strength, combined with other layered security controls, can more effectively mitigate risks associated with authentication," states the FFIEC bulletin.
The Financial-grade API (FAPI) Security Profile takes it further. "The protected resources that conform to this document shall not accept a bearer access token. They shall only support sender-constrained access tokens via MTLS," according to the OpenID Foundation specification.
Sender-constrained tokens bind the token to the client's TLS certificate. Even if an attacker steals the token, they cannot use it without the corresponding private key.
RFC 8693 defines a protocol for an HTTP- and JSON-based Security Token Service (STS) that extends OAuth 2.0 to enable the exchange of security tokens, including tokens employing impersonation and delegation. This specification is particularly relevant for fintech compliance, as it supports secure and efficient token exchanges necessary for regulatory adherence.
Key takeaway: Bearer tokens are a liability. Migrate to sender-constrained tokens and enforce MFA on every privileged operation.
Deploying Gateways at Scale: IaC, IDPs & Industry Clouds
Infrastructure as code (IaC) enables consistent cloud implementation practices and ensures consistent deployment and management of infrastructure resources. Gartner notes that IaC enables an "application-down" approach, integrating applications with their infrastructure.
Industry cloud platforms (ICPs) are designed to meet the specific needs of vertical industry segments inadequately served by generic solutions. "By 2027, more than 70% of enterprises will use industry cloud platforms to accelerate their business initiatives, up from less than 15% in 2023," according to Gartner.
For MCP Gateway deployments, the playbook is:
- Define gateway configurations in YAML (convert legacy APIs to MCP servers without code changes)
- Use Kubernetes and Helm for multi-replica deployments
- Integrate with Internal Developer Platforms (IDPs) to give developers self-service access while maintaining governance
The Pulumi blog highlights key metrics for IDP success: "reduced time-to-market through faster infrastructure provisioning," "improved developer productivity by eliminating infrastructure bottlenecks," "enhanced security posture through consistent policy enforcement," and "lower operational overhead through standardization and automation," per Pulumi.
Real-world results back this up. Starburst Data cut their infrastructure deployments from two weeks to just three hours using IDP-driven automation.
Secrets Management & Rotation
Uber's engineering team provides a masterclass in secrets management at scale. "At Uber, we run over 5,000 microservices, 5,000 databases, and over 500,000 analytical jobs per day to support millions of people worldwide using our apps," they write. "Over 150,000 secrets facilitate authentication among these large, distributed ecosystems," per Uber Engineering.
Key initiatives from Uber's playbook:
- Pre-commit CLI tool: Blocks commits containing secrets before they reach the repository
- Vault consolidation: Converged 25 secret vaults across multiple clouds into 6 managed by a single team
- Automatic rotation: "This system orchestrated automatic rotation for 20,000 secrets per month on average, without any human involvement," per Uber Engineering
For MCP Gateways, secrets rotation is non-negotiable. OAuth tokens, API keys, and TLS certificates must rotate on a schedule that limits blast radius if a credential leaks.
How Do Gateways Beat Direct API Hooks (Leaving Adyen & Stripe Catching Up)?
Traditional payment gateway integrations require choosing between user experience and compliance burden. "Typically, Payment Gateways offer a variety of integration methods, each with a different user experience and different technical requirements," notes Thoughtworks.
The four common methods (hosted payment page, in-context popup, iFrame, API) differ in terms of PCI requirements on the merchant's website and development costs. API integration delivers the best customer experience but demands full PCI DSS compliance.
MCP Gateways flip the equation:
| Direct API Hooks | MCP Gateway |
|---|---|
| Requires code changes for each integration | Configuration-driven (YAML) |
| PCI scope expands with each endpoint | Single enforcement point |
| Manual audit trail stitching | Centralized, tamper-proof logs |
| No protocol-level agent verification | Native support for Visa/Mastercard agentic protocols |
Adyen and Stripe offer robust platforms. Adyen provides "end-to-end payments, data, and financial management in a single solution," while Stripe "handles billions of dollars every year for forward-thinking businesses," according to a SourceForge comparison. Both support omnichannel payments and extensive payment methods.
However, neither platform natively addresses the agentic commerce layer. As AI agents increasingly initiate transactions, fintechs need a gateway that speaks MCP, validates agent identity via protocols like Visa's Trusted Agent Protocol, and logs every tool call for audit.
MCP Gateway is "platform-agnostic, supports deployment on bare metal, VMs, ECS, Kubernetes, etc., without modifying existing infrastructure," per the mcp-gateway repository. That zero-intrusion model means fintechs can layer gateway controls on top of existing Adyen or Stripe integrations without ripping and replacing.
Next Steps: From Compliance Cost Center to Competitive Edge
Compliance is often framed as a cost center. It does not have to be.
Audit trails, when done right, provide a log of evidence that offers insights for security and audit teams, aiding in identifying suspicious activities, evidencing non-compliance, and uncovering the root cause of issues. That same data powers fraud detection, customer analytics, and operational optimization.
IaC drives productivity improvements for application teams and technical users. The same automation that ensures compliant deployments also accelerates time-to-market and reduces operational overhead.
The action plan:
- Audit your MCP server exposure. If you have servers without authentication proxies, prioritize remediation.
- Map your compliance stack. Identify gaps across PCI DSS 4.0.1, OFDSS, and Open Banking guidelines.
- Deploy an MCP Gateway. Start with a pilot workload, validate audit logging, and expand.
- Integrate with your IDP. Give developers self-service access within guardrails.
- Automate secrets rotation. No human involvement should be required for routine credential updates.
Golf offers the infrastructure to build, deploy, and monitor MCP Gateways that meet fintech compliance requirements. If you are a VP of Engineering or AppSec Lead blocking AI roadmaps due to data leakage risks or compliance fears, deploy a single-workflow MCP server and monitor protocol-aware observability today.
Frequently Asked Questions
What is an MCP Gateway?
An MCP Gateway is a lightweight proxy layer that converts legacy APIs into compliant, observable endpoints without rewriting code, ensuring secure interactions between AI agents and sensitive financial systems.
Why are MCP Gateways important for fintech compliance?
MCP Gateways are crucial for fintech compliance as they enforce token delegation, audit logging, and pre-authentication, maintaining PCI DSS and Open Banking controls even as agentic traffic scales.
What are the key components of the 2025 compliance stack?
The 2025 compliance stack includes PCI DSS 4.0.1, OFDSS, and Open Banking guidelines, focusing on encrypted transport, strong access controls, provable audit trails, and sender-constrained tokens.
How does an MCP Gateway enhance security?
An MCP Gateway enhances security by providing a proxy, delegation, and observability layers, which convert APIs to MCP-compliant services, grant user-specific access tokens, and log every tool call for audit retrieval.
How can fintechs deploy MCP Gateways at scale?
Fintechs can deploy MCP Gateways at scale using infrastructure as code (IaC), Kubernetes, and Helm for multi-replica deployments, integrating with Internal Developer Platforms (IDPs) for self-service access and governance.
Sources
- https://www.trendmicro.com/vinfo/us/security/news/cybercrime-and-digital-threats/mcp-security-network-exposed-servers-are-backdoors-to-your-private-data
- https://cardchamp.com/blog/how-to-become-pci-compliant-a-guide-for-payment-gateways
- https://docs.aws.amazon.com/wellarchitected/latest/devops-guidance/ag.ca.1-establish-comprehensive-audit-trails.html
- https://workos.com/blog/mcp-security-risks-best-practices
- https://ofdss.org/
- https://standards.openbanking.org.uk/good-practice/other-introduction/v3-1-11
- https://www.digitalcommerce360.com/2025/10/16/visa-mastercard-both-launch-agentic-ai-payments-tools/
- https://developer.visa.com/capabilities/trusted-agent-protocol/trusted-agent-protocol-specifications
- https://github.com/mcp-ecosystem/mcp-gateway
- https://aircconline.com/csit/papers/vol15/csit150908.pdf
- https://docs.hcxprotocol.io/hcx-technical-specifications/open-protocol/audit
- https://docs.aws.amazon.com/whitepapers/latest/navigating-gdpr-compliance/collecting-and-processing-logs.html
- https://www.pynt.io/blog/llm-security-blogs/state-of-mcp-security
- https://www.paloaltonetworks.sg/resources/guides/simplified-guide-to-model-context-protocol-vulnerabilities
- https://occ.gov/news-issuances/bulletins/2021/bulletin-2021-36a.pdf
- https://openid.net/specs/openid-financial-api-part-2-1_0.html
- https://andrew-scott.co.uk/docs/rfc-pdf/rfc8693.pdf
- https://www.gartner.com/en/articles/infrastructure-as-code
- https://www.gartner.com/en/articles/what-are-industry-cloud-platforms
- https://www.pulumi.com/blog/idp-strategy-planning-self-service-infrastructure-that-balances-developer-autonomy-with-operational-control/
- https://www.uber.com/en-GB/blog/building-ubers-multi-cloud-secrets-management-platform/
- https://thoughtworks.com/en-gb/insights/blog/ethical-tech/how-to-select-a-payment-gateway--part-4---payment-gateways-integ
- https://sourceforge.net/software/compare/Adyen-vs-PayPal-vs-Stripe/
