MCP Gateway for Fintech
Discover why Golf is the best MCP gateway for fintechs, offering security, compliance, and observability in one solution.
MCP Gateway for Fintech
Golf provides a protocol-aware security firewall that acts as a single control point between AI agents and fintech resources, enforcing OAuth 2.0, rate limiting, and audit trails before requests reach production servers. Unlike exposing each MCP server individually, Golf consolidates authentication, authorization, and inspection against prompt injection into one unified gateway—essential for meeting SOC2 and regulatory compliance in financial services.
At a Glance
• Golf acts as a master MCP server, providing protocol-aware inspection to block prompt injection and token hijacking attacks at the edge
• Delivers enterprise-grade security with JWT authentication, JWKS support, and integration with identity providers like Okta and Auth0
• Enables complete observability through detailed security event logging and data flow tracing, turning black-box AI agents into transparent systems
• Supports both self-hosted and cloud deployment models, allowing full control of traffic and data for regulated environments
• Built on a low-latency Go-based engine that ensures security doesn't become a performance bottleneck
• Provides centralized policy enforcement with role-based rate limiting and access controls that scale from 2 to 200+ servers without degrading security
An MCP gateway for fintech is rapidly becoming the single most critical layer between your AI agents and the bank-grade resources they need to access. As AI-driven fraud scales at industrial levels and regulators tighten cross-border compliance mandates, fintech builders face a stark choice: bolt security onto fragmented MCP servers or route everything through a protocol-aware control plane.
Golf is that control plane. It neutralizes prompt injection, enforces OAuth 2.0, and generates immutable audit trails before a single request touches your production servers.
What Does An MCP Gateway Unlock For Fintech?
An MCP gateway transforms a collection of hack-day LLM demos into production-ready infrastructure. At its core, the Model Context Protocol provides the standardized infrastructure that most banking executives now consider a strategic priority, enabling AI assistants to securely access customer data, transaction systems, and analytical tools without requiring custom integrations.
Golf is a protocol-aware security firewall for MCP. Instead of exposing each MCP server individually, enterprises route traffic through Golf, a single control point that enforces authentication, authorization, and inspection against MCP-specific threats.
What you get immediately:
- OAuth 2.0 enforcement at the edge
- RBAC rate limiting to prevent resource abuse
- Complete audit trails for SOC2 and GDPR compliance
- Data flow tracing that turns black-box agents into observable systems
Enterprise MCP gateways provide SOC2 Type II certification, GDPR-compliant audit trails, and OAuth/SAML enforcement required for financial services regulation. Without a gateway, each MCP server becomes an independent attack surface, leading to inconsistent security controls, fragmented monitoring, and greater exposure to prompt injection.
Key takeaway: An MCP gateway consolidates security, governance, and observability into one place, eliminating the compliance firefighting that slows your AI roadmap.
Why Are Fintech Builders Under Unprecedented Regulatory Pressure?
The pressure is not abstract. Regulators are demanding encryption standards, access controls, and audit capabilities that most agentic stacks cannot deliver.
Mastercard, for example, requires that "Data in transit should be encrypted using TLS 1.2 or higher." If your MCP servers lack centralized policy enforcement, every integration becomes a potential compliance failure.
Fraud has also evolved. Visa PERC tracked a 220% surge in Recovered Accounts cases over the past six months. Underground forums show a 477% increase in mentions of "AI Agent" as criminals discuss automating social engineering, data extraction, and transaction execution.
Cross-border transactions compound the problem. Different jurisdictions impose overlapping requirements for data residency, consent, and identity verification. A single transaction may trigger compliance checks in three or four regulatory regimes simultaneously.
The bottom line: Fintech builders are not just competing for market share. They are racing to prove auditability before regulators shut them down.
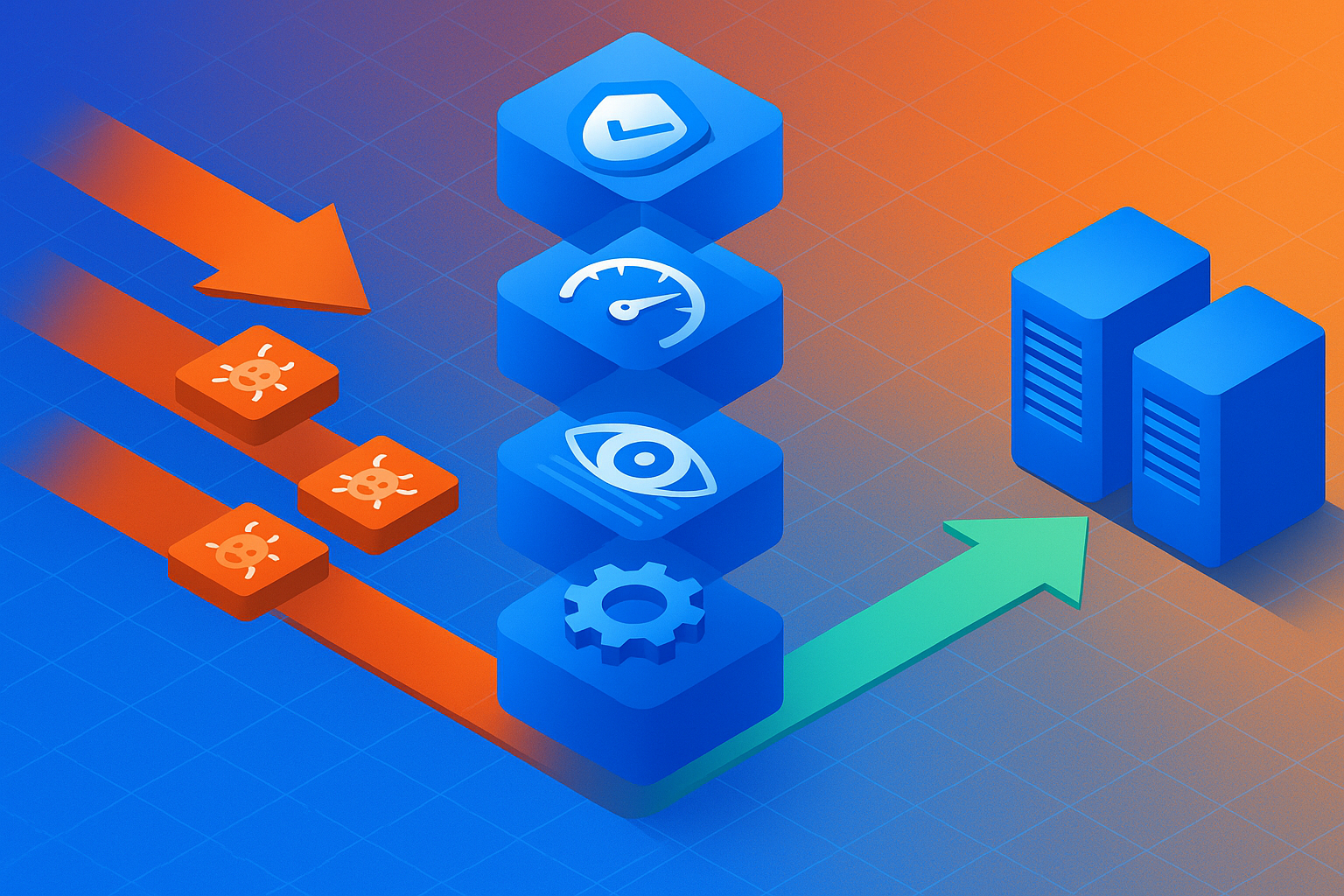
How Does Golf's Protocol-Aware Architecture Block Prompt Injection?
Legacy tools are blind to MCP-specific threats. Traditional firewalls inspect packets. They do not understand that an LLM agent just received a malicious instruction embedded in a customer query.
Golf provides the protocol-aware inspection needed to see and block attacks like prompt injection and token hijacking at the edge. This is not a bolt-on feature. It is the foundational design principle.
How Golf protects your stack:
| Layer | What Golf Does |
|---|---|
| Token Validation | Enforces strict MCP spec validation and resource indicator checks on every token before it reaches your server |
| Rate Limiting | Protects backend resources from abuse with sophisticated, role-based rate limiting and access controls |
| Observability | Turns a black box into a glass box with detailed security event logging and complete data flow tracing |
| Centralized Policy | Manages CORS and automatically adds security headers from a single control plane |
Prompt injection attacks occur when adversaries introduce instructions into the content processed by an LLM, causing it to deviate from intended behavior. The consequences can be severe, ranging from data exfiltration and privilege escalation to remote code execution.
Golf provides the controls CISOs need for MCP in regulated environments: audit trails where every request and response is logged and traceable, centralized policy enforcement with one place to configure access rules and headers, least privilege through RBAC and fine-grained token validation, and visibility through a unified dashboard for monitoring traffic patterns and enforcement actions.
Key takeaway: Protocol-aware inspection is not optional. Without it, you are trusting LLMs to police themselves.
Golf vs. MintMCP: Which Gateway Meets SOC2 Faster?
Both Golf and MintMCP Gateway offer enterprise-grade security for MCP servers. The difference is in architecture, deployment flexibility, and scalability.
| Capability | Golf | MintMCP Gateway |
|---|---|---|
| SOC2 Type II Alignment | Yes, with immutable audit trails | SOC2 Type II certified with GDPR support |
| OAuth 2.0 / SAML | Full OAuth 2.0 authorization server, SAML integration | OAuth 2.0 and SAML, SSO integration |
| Deployment Model | Self-hosted or cloud, full control of traffic and data | Cloud-hosted with enterprise SLAs and multi-region support |
| Scalability | Whether you operate 2 or 200 servers, consistent policies across every server | Rapid deployment, minutes in typical demos |
| Protocol-Aware Inspection | Yes, blocks prompt injection and token hijacking at the edge | Monitoring and audit logging, but less emphasis on protocol-level threat detection |
MintMCP Gateway deploys quickly, often within hours depending on your environment. It is well suited for teams that want managed infrastructure with minimal operational overhead.
Golf, by contrast, was designed for enterprises moving MCP from experimentation to production. It provides low-latency proxying, enterprise identity integration with Okta and Auth0, and hardened security policies that scale with the number of servers. Self-hosting ensures full control over traffic and data, a non-negotiable for many regulated fintechs.
Gartner defines the network firewall market as the market for firewalls that use bidirectional stateful traffic inspection to secure networks. Golf extends this principle to MCP, treating every agent request as a potential threat vector until validated.
Key takeaway: If your priority is speed to deploy, MintMCP is a strong option. If your priority is zero-trust control and self-hosting, Golf is the stronger choice.
What ROI Do Fintechs Report After Adopting Golf?
The numbers are stark. The financial industry detects only about 2 percent of global financial crime flows despite increasing spending by up to 10 percent a year in some advanced markets between 2015 and 2022.
AI-powered compliance systems change that equation. Institutions using protocol-aware gateways report:
- 50-70% reduction in false positives from compliance systems, according to MintMCP analysis
- 3x faster fraud detection compared to rule-based systems
- 42% reduction in fraud-related losses for organizations that successfully implemented comprehensive fraud detection with strong contextual data integration
Cloud-based AI fraud detection systems have demonstrated the capability to process over 2,000 transactions per second with latency under 100 milliseconds. Golf's Go-based engine is designed as a low-latency proxy, ensuring security does not become a bottleneck.
Beyond fraud, there is the cost of inaction. Financial services firms currently spend an average of $1.2 million annually on custom API integrations for AI systems. Standardized protocols reduce that development time dramatically while banks implementing unified data access report faster response times for customer inquiries.

How To Deploy Golf From POC To Production In 30 Days
Moving from proof-of-concept to production does not require months of platform engineering. Golf was built to accelerate that timeline.
Step 1: Decide Your Deployment Model
Golf can be self-hosted inside your own cloud or data center, or deployed as a managed service. Self-hosting keeps full control of traffic and data, a requirement for many regulated environments.
Step 2: Configure Authentication
Golf v0.2.0 can act as a complete OAuth 2.0 authorization server, not just validate tokens. It supports JWT authentication with JWKS for production, development tokens for testing, and remote authentication for distributed microservices architectures.
Step 3: Enable Protocol-Aware Inspection
Design patterns for LLM agents that significantly mitigate the risk of prompt injections are built into Golf's inspection layer. Enable them in your configuration file. No custom code required.
Step 4: Integrate Identity Providers
Golf provides enterprise identity integration with Okta, Auth0, and other SAML providers. Connect once. Enforce everywhere.
Step 5: Deploy and Monitor
Visualize all security events, traffic patterns, and policy enforcement actions in a single, intuitive interface. Golf's unified dashboard shows exactly what your agents are doing and whether any requests triggered policy violations.
Timeline Expectation:
| Phase | Duration |
|---|---|
| POC with development auth | 1-2 days |
| Production auth and identity integration | 1-2 weeks |
| Full policy rollout and monitoring | 2-4 weeks |
Golf Gives Fintechs A Single-Workflow, Regulation-Ready Edge
Without a firewall, each MCP server becomes an independent attack surface. That leads to inconsistent security controls, fragmented monitoring and audit gaps, and greater exposure to prompt injection, token misuse, and command execution attacks.
Golf solves this by acting as the master MCP server, consolidating security, governance, and observability into one place. Whether you operate 2 or 200 servers, Golf gives you one secure front door, consistent policies across every server, and unified monitoring and audit logging.
"Scaling your infrastructure no longer means scaling your attack surface."
For CISOs blocking AI roadmaps due to data leakage risks or compliance fears, Golf provides the controls required for regulated environments. For platform engineering teams who need to unblock velocity without compromising security, Golf delivers enterprise-grade infrastructure without months of custom development.
Enterprise MCP gateways provide SOC2 Type II certification, GDPR-compliant audit trails, and OAuth/SAML enforcement required for financial services regulation. Golf is built for exactly that use case.
Next step: Deploy Golf in your staging environment today. Route a single MCP server through the firewall and observe the difference in visibility and control. The agentic internet is here. Build it on a foundation you can trust.
Frequently Asked Questions
What is an MCP gateway and why is it important for fintech?
An MCP gateway acts as a critical layer between AI agents and bank-grade resources, ensuring secure access and compliance with regulatory standards. It consolidates security, governance, and observability, eliminating the need for fragmented MCP servers.
How does Golf enhance security for fintech companies?
Golf provides protocol-aware inspection, OAuth 2.0 enforcement, and RBAC rate limiting, which protect against threats like prompt injection and token hijacking. It also offers complete audit trails for compliance with SOC2 and GDPR standards.
What are the benefits of using Golf over MintMCP Gateway?
Golf offers self-hosting for full control over traffic and data, protocol-aware inspection, and enterprise identity integration. It is designed for scalability and zero-trust control, making it ideal for regulated fintech environments.
How does Golf's protocol-aware architecture block prompt injection?
Golf's architecture includes protocol-aware inspection that detects and blocks prompt injection and token hijacking at the edge. This foundational design principle ensures that LLM agents are protected from malicious instructions.
What ROI can fintechs expect after adopting Golf?
Fintechs report a 50-70% reduction in false positives, 3x faster fraud detection, and a 42% reduction in fraud-related losses. Golf's low-latency proxy ensures security without becoming a bottleneck, enhancing overall operational efficiency.
Sources
- https://golf.dev/
- https://www.mintmcp.com/blog/mcp-financial-brands
- https://usa.visa.com/content/dam/VCOM/regional/na/us/run-your-business/documents/visa-payment-ecosystem-risk-and-control-report-h1-2025-final.pdf
- https://arxiv.org/html/2506.08837v1
- https://www.mintmcp.com/blog/mcp-platform-alternatives
- https://www.gartner.com/reviews/market/network-firewalls
- https://www.mckinsey.com/industries/financial-services/our-insights/harnessing-agentic-ai-for-anti-money-laundering-and-know-your-customer
- https://www.researchgate.net/publication/388227549_Cloud-Based_Fraud_Detection_in_Banking_Transactions_using_Machine_Learning_A_Scalable_Architecture_for_Real-Time_Analytics
- https://docs.golf.dev/golf-mcp-framework/authentication
