Golf's Open-Source MCP Gateway for Fintech Security
Discover how Golf's open-source MCP gateway enhances fintech security by blocking AI-native threats and ensuring compliance.
Golf's Open-Source MCP Gateway for Fintech Security
Golf's open-source MCP gateway provides fintech teams with protocol-aware security controls for AI agent deployments. It addresses unique security challenges introduced by the Model Context Protocol through JWT authentication, policy-enforced routing, and audit logging that meets SOC 2 and FFIEC compliance requirements while maintaining sub-10ms latency for financial workloads.
At a Glance
• The Model Context Protocol enables standardized AI-to-system connections but introduces new attack vectors including prompt injection and tool poisoning with up to 72.8% success rates
• Security researchers discovered 492 exposed MCP servers lacking authentication or encryption, exposing proprietary data
• Golf's gateway implements OAuth 2.1, JWT validation, and protocol-aware observability for complete audit trails
• Performance benchmarks show throughput above 91,000 requests per second with P99 latency under 10ms
• Block reduced data platform integration time from weeks to minutes using secure MCP deployments
• JPMorgan Chase and Barclays leverage open protocols for regulatory compliance and process automation at scale
Open-source MCP gateway sits at the heart of fintech security. Regulated teams need it now because AI agents are connecting to sensitive financial systems at unprecedented speed, and the protocol that standardizes those connections, the Model Context Protocol, introduces risks that legacy security tools cannot address.
MCP is like a USB-C port for AI agents, a standardized link that greatly reduces the headaches of connecting large language models to tools and data. But that standardization also opens new attack vectors. Security researchers have already found 492 exposed servers with no client authentication or traffic encryption, exposing company proprietary information and customer details to potential breach.
For fintech teams, the stakes are existential. A gateway that speaks the protocol while blocking prompt-level threats and maintaining audit trails is not optional. It is the difference between deploying AI responsibly and inviting compliance failure.
Why Fintech Needs an Open-Source MCP Gateway -- Fast
MCP is an open protocol spearheaded by Anthropic that defines a standardized interface for connecting Large Language Models with external data sources and tools. Instead of writing custom integrations for every data system, teams build once to the MCP specification and connect everywhere.
The value of a gateway becomes clear when you consider what sits on the other side: customer account data, transaction histories, compliance workflows. Without a policy-enforced proxy, every tool invocation is a potential data leak. Every prompt is a potential injection vector.
"MCP gives LLMs and agents the context they need to take real action," as Block's engineering team observed when deploying the protocol across their data platforms. That power demands control.
The urgency is compounded by adoption velocity. Gartner projects that by 2026, 75% of API gateway vendors will have MCP features. Financial institutions cannot wait for the ecosystem to mature. They must secure the protocol now, on their terms.
Key takeaway: An open-source MCP gateway gives fintech teams the control to deploy AI agents without ceding security to third-party vendors or waiting for the protocol to bake in protections that regulators already require.

What AI-Native Threats Does an MCP Gateway Block?
The Model Context Protocol's server-based architecture introduces unique security challenges that traditional firewalls and API gateways were never designed to address. The threat model is different because the attack surface includes natural language itself.
A properly designed gateway neutralizes four primary threat categories:
- Prompt injection -- Malicious instructions embedded in external content that hijack agent behavior
- Tool poisoning -- Hidden instructions in MCP tool descriptions that execute without user awareness
- Data exfiltration -- Sensitive information leaked through side-channel communication
- Cross-server attacks -- Exploits that leverage AI agents' instruction-following behavior across multiple servers
The evaluation of 20 prominent LLM agents revealed widespread vulnerability to tool poisoning, with o1-mini achieving an attack success rate of 72.8%. These are not theoretical risks. They are reproducible exploits against production models.
Indirect Prompt Injection
"Indirect prompt injection refers to attacks via malicious prompts placed in any source the AI agent interacts with, which is not added via the user input," according to MCP security researchers.
The pattern is called XPIA, cross-domain prompt injection. An attacker embeds instructions in a document, email, or database record. The AI agent retrieves that content as context, interprets the embedded instructions as legitimate, and executes them.
For fintech, the impact is severe. An XPIA attack against a customer service agent could exfiltrate account numbers. An attack against a compliance agent could suppress suspicious activity alerts. The agent does exactly what it was designed to do: follow instructions. It simply cannot distinguish between legitimate context and weaponized content.
Researchers demonstrated that prompt injection attacks can covertly force agents to invoke malicious logging tools to exfiltrate sensitive information including user queries, tool responses, and agent replies. The attack preserves normal task completion while silently capturing every interaction.
Tool Poisoning Benchmarks
Tool poisoning is particularly insidious because the malicious payload lives in the tool's metadata, not in user input or external documents. The agent never sees a suspicious prompt. It simply reads a tool description that contains hidden instructions.
The MCPTox benchmark quantifies the exposure:
- 45 real-world MCP servers tested across 353 authentic tools
- 1,312 malicious test cases spanning 11 distinct risk categories
- 72.8% attack success rate against the most vulnerable model tested
- Less than 3% refusal rate even for the best-aligned model (Claude-3.7-Sonnet)
The low refusal rates are the critical finding. Existing safety alignment is ineffective against malicious actions that use legitimate tools for unauthorized operations. The attack does not trigger safety filters because it does not look like an attack. It looks like normal tool invocation.
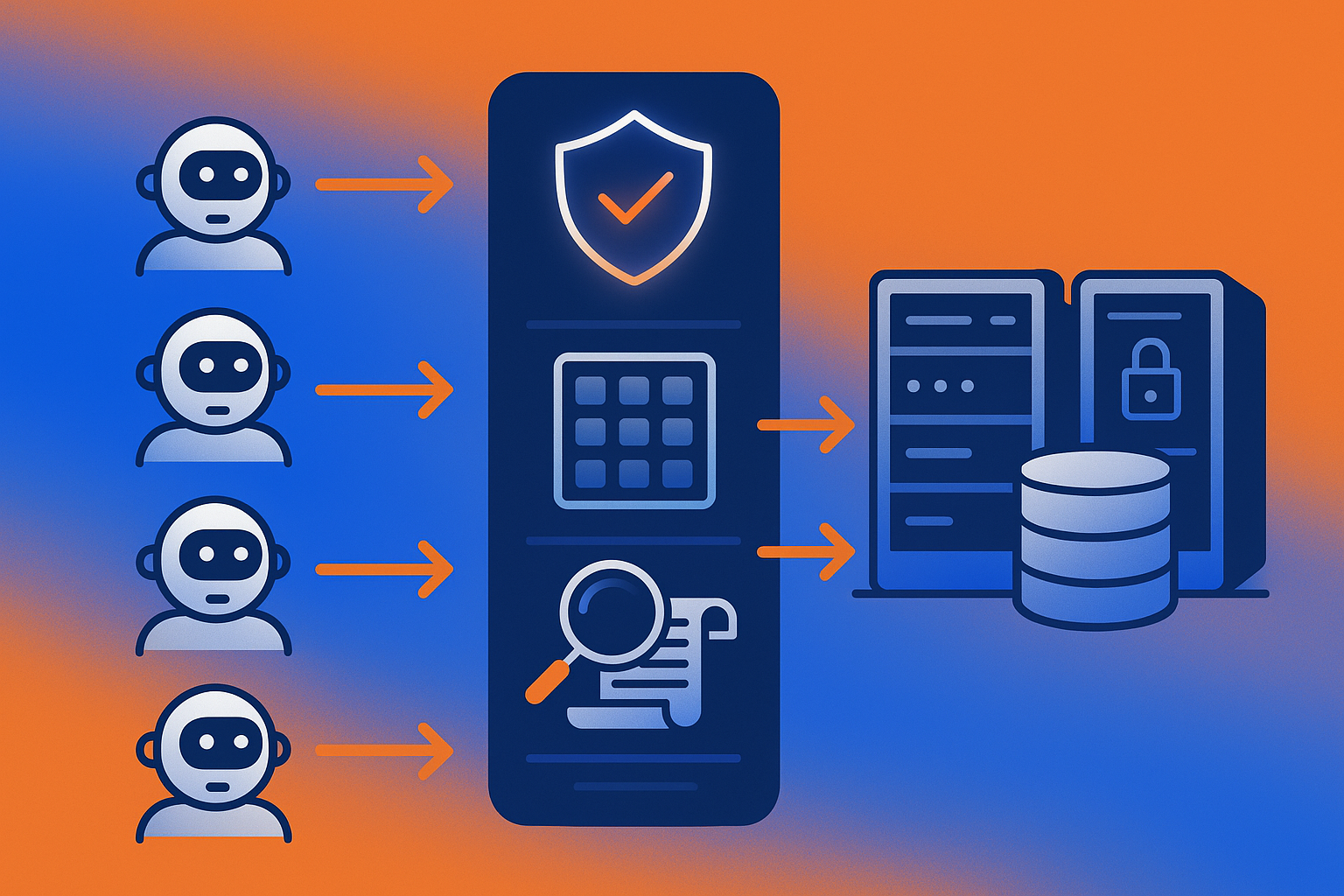
How Is Golf's Open-Source MCP Gateway Built?
Golf's gateway architecture addresses the AI-native threat model with three layers: authentication that establishes identity at the protocol boundary, routing that enforces policy on every tool invocation, and observability that creates the audit trail regulators require.
OAuth 2.0 plays a pivotal role in securing MCP servers by providing a standardized framework for authentication and authorization. The gateway implements this framework with the additional controls that fintech environments demand.
The MCP tool allows you to pass custom headers, such as authentication keys or schemas, that a remote MCP server might need. Golf's gateway intercepts these headers, validates them against policy, and logs the transaction before forwarding to the upstream server.
Layered AuthZ -- JWT, API Keys, and OAuth 2.1
GolfMCP provides flexible authentication mechanisms to secure MCP servers:
- JWT Authentication -- Enterprise-grade authentication with JWKS support for production environments requiring standards-compliant token validation
- OAuth 2.1 Server -- Full authorization server functionality, enabling Golf to issue and validate tokens directly rather than depending on external identity providers
- API Key Authentication -- Pass-through authentication to upstream APIs for legacy system integration
- Remote Authentication -- Distributed authentication across multiple resource servers for organizations with federated identity architectures
Fintech regulators prefer these mechanisms because they align with existing compliance frameworks. The Model Context Protocol is an open standard for connecting AI applications to external data sources, tools, and workflows through a consistent interface. Auth0's approach to MCP security emphasizes OAuth 2.1 and OpenID Connect for user authentication, controlled API access, and scoped token exchange.
The authorization server should allow fine-grained scopes and claims to ensure tokens issued to AI agents follow the principle of least privilege. Golf implements this through configurable scope policies that limit what each agent can access based on role, time of day, or transaction type.
Protocol-Aware Observability
Zero-trust architectures require continuous validation. The gateway must log not just that a request occurred, but what the request contained, what the agent did with it, and what data flowed back.
Audit logs capture detailed data, such as timestamps, user identifiers, IP addresses, and event outcomes. For MCP traffic, the logs must also capture tool names, parameter values, and response content. This is protocol-aware observability: understanding the semantics of MCP requests, not just the bytes on the wire.
The tool uses protocol-aware observability to monitor data integrity and alert users to anomalies. When a tool invocation deviates from expected patterns, when an agent requests data outside its normal scope, when a response contains content that matches PII patterns, the observability layer flags the event for review.
For compliance teams, this logging provides the provable chain of custody that auditors require. Every decision traces back to an OAuth-scoped identity. Every data access ties to a business justification.
Building for SOC 2 and FFIEC: Compliance by Design
SOC 2 compliance is not a checkbox exercise. It is a framework that shapes how organizations handle customer data at every level of the stack. The 2017 Trust Services Criteria established by AICPA cover security, availability, processing integrity, confidentiality, and privacy. An MCP gateway must address all five.
The FFIEC guidance on Authentication and Access to Financial Institution Services is equally relevant. It replaces earlier guidance from 2005 and 2011, acknowledging the evolving cybersecurity threat landscape. The guidance emphasizes that when a risk assessment indicates single-factor authentication is inadequate, multi-factor authentication or controls of equivalent strength must be implemented.
Golf's gateway aligns with these frameworks through:
- Centralized audit trails -- Every tool invocation logged with identity, timestamp, and outcome
- Encryption at rest and in transit -- TLS 1.2 or later for all communications, with certificate management built into the deployment
- Role-based access control -- Scopes and claims that limit agent capabilities to business requirements
- Incident reporting hooks -- Integration with SIEM platforms for real-time alerting
The FCA has noted that since 2018, over 20% of operational incident reports submitted by firms arrived over 11 days after the incident began. The gateway's real-time observability helps teams detect and report incidents within the timeframes regulators expect.
Why Gateway Throughput Matters When Every Millisecond Equals Money
Fintech workloads have hard latency requirements. A payment authorization that takes 500ms instead of 50ms is a failed transaction. A trading system that adds 100ms per request loses money on every trade.
The conventional approach, deploying a perimeter web application firewall to protect applications, is no longer enough. Legacy WAFs were designed for HTTP request filtering, not for inspecting the semantic content of MCP tool invocations.
Performance benchmarks reveal the gap:
| Solution | Requests Per Second | P99 Latency |
|---|---|---|
| NGINX App Protect WAF | ~19,000 | Lowest tested |
| Cloudflare WAF | ~14,000 | Moderate |
| AWS WAF | ~6,000 | 10x higher than NGINX |
| Azure WAF | ~2,000 | Highest tested |
Source: GigaOm High-Performance WAF Testing
Kong's maximum transactions per second throughput, achieved with 100% success and less than 30ms maximum latency, was 54,250. This establishes the baseline for what a purpose-built gateway can achieve.
Kong Gateway benchmarks on AWS infrastructure show 127,257 RPS with P99 latency of 7.11ms for basic proxy operations. With rate limiting and key authentication enabled, throughput remains above 91,000 RPS with P99 under 10ms.
The implication for MCP gateways is clear: the inspection layer cannot be a bottleneck. Golf's architecture processes MCP requests in the same latency envelope as standard API traffic, adding security without sacrificing the milliseconds that fintech workloads cannot afford to lose.
Real-World Wins: Block, Barclays, and JPMorgan Chase
Fintech institutions are already proving the value of standardized, secure AI integration.
Block deployed MCP across their data platforms using Goose, their open-source AI agent. As Sam Osborn from Block's team noted, "Something that might have taken hours, or days, or even weeks turns into just a few simple, short conversation messages."
Block's data environment spans over 50 platforms with different ownership models, access controls, and compliance requirements. The MCP server acts as a standardized bridge that gives AI agents direct, governed access to organizational metadata. The governance layer is critical: agents can query data, but they cannot bypass access controls or leak information outside approved channels.
Barclays revamped their post-trade settlements to a "settlements as a service" model, decomposing monolithic systems into microservices. The implementation began with cash settlements, handling about 35,000 daily processes with plans to scale up to half a million per day. The architecture emphasizes real-time visibility and process orchestration, exactly the capabilities that an MCP gateway enables for AI workloads.
JPMorganChase's derivatives business leverages the FINOS Common Domain Model and ISDA Digital Regulatory Reporting. The bank was recognized with the "Adoption Achiever" award at the Open-Source Finance Forum. Their goal was simplification within the regulatory reporting landscape, which has evolved constantly over the last decade. Open protocols, including MCP for AI integration, are central to that simplification.
Secure the Agentic Future -- Starting With Your Gateway
The agentic internet is here. AI agents are connecting to financial systems, executing transactions, and making decisions that affect customers and markets. The question is not whether to deploy these agents, but how to deploy them securely.
Start with the gateway. JWT authentication provides enterprise-grade security with JWKS support, the recommended approach for production environments where you need standards-compliant token validation. Golf v0.2.0 can act as a complete OAuth 2.0 authorization server, not just validate tokens.
The build system supports standard Python repository structures for organizing shared code, making it straightforward to integrate with existing fintech infrastructure. Multiple components can share utility functions, client initializations, and Pydantic models without duplicating code or introducing inconsistency.
Action: Deploy Golf's open-source MCP gateway in your staging environment this week. Configure JWT authentication against your existing identity provider. Enable protocol-aware logging to your SIEM. Run your AI agents through the gateway and review the audit trail.
The agentic future rewards teams that move fast without breaking trust. Golf gives you the control to do both.
Frequently Asked Questions
What is the Model Context Protocol (MCP)?
The Model Context Protocol (MCP) is an open protocol that standardizes the connection between large language models and external data sources, reducing integration complexity but introducing new security risks.
Why is an open-source MCP gateway crucial for fintech?
An open-source MCP gateway is essential for fintech because it provides control over AI agent deployments, ensuring security and compliance without relying on third-party vendors.
What threats does an MCP gateway address?
An MCP gateway addresses threats like prompt injection, tool poisoning, data exfiltration, and cross-server attacks, which traditional security tools cannot effectively mitigate.
How does Golf's MCP gateway enhance security?
Golf's MCP gateway enhances security through layered authentication, policy enforcement on tool invocations, and protocol-aware observability, ensuring compliance and data integrity.
What are the compliance benefits of using Golf's MCP gateway?
Golf's MCP gateway aligns with SOC 2 and FFIEC frameworks, providing centralized audit trails, encryption, role-based access control, and real-time incident reporting to meet regulatory requirements.
Sources
- https://promptfoo.dev/docs/red-team/mcp-security-testing
- https://arxiv.org/pdf/2508.14925
- https://www.trendmicro.com/vinfo/us/security/news/cybercrime-and-digital-threats/mcp-security-network-exposed-servers-are-backdoors-to-your-private-data
- https://www.bcg.com/publications/2025/put-ai-to-work-faster-using-model-context-protocol
- https://developer.microsoft.com/blog/protecting-against-indirect-injection-attacks-mcp
- https://datahub.com/blog/datahub-mcp-server-block-ai-agents-use-case
- https://www.k2view.com/blog/mcp-gartner/
- https://mcpmanager.ai/blog/mcp-prompt-injection/
- https://openreview.net/pdf/c2567f59e9e1559bede97fb86ef23287d3b3b5bd.pdf
- https://www.csoonline.com/article/4015222/mcp-uses-and-risks.html
- https://developer.pingidentity.com/identity-for-ai/agents/idai-securing-mcp-servers.html
- https://learn.microsoft.com/en-us/agent-framework/user-guide/model-context-protocol/
- https://docs.golf.dev/golf-mcp-framework/authentication
- https://auth0.com/ai/docs/mcp/auth-for-mcp
- https://security.cms.gov/policy-guidance/audit-and-accountability-au-handbook
- https://invariantlabs.ai/blog/mcp-security-notification-tool-poisoning-attacks
- https://us.aicpa.org/content/dam/aicpa/interestareas/frc/assuranceadvisoryservices/downloadabledocuments/trust-services-criteria.pdf
- https://occ.gov/news-issuances/bulletins/2021/bulletin-2021-36a.pdf
- https://www.fca.org.uk/publication/consultation/cp24-28.pdf
- https://gigaom.com/report/high-performance-web-application-firewall-testing/
- https://gigaom.com/report/api-and-microservices-management-benchmark-3/
- https://docs.konghq.com/gateway/3.10.x/production/performance/
- https://camunda.com/case-study/barclays
- https://www.jpmorganchase.com/about/technology/blog/jpmc-launches-finos-open-source-solution
- https://docs.golf.dev/golf-mcp-framework/shared-logic-common-py
